Morphick’s Iterative Incident Response Process
Upfront Partnering
- A 24x7x365 always-on Incident Response team
- A dedicated team of Reverse Engineers to analyze malicious files
- An experienced team of intrusion analysts to track and hunt your adversaries
- A clearly defined contract with agreed upon terms and rates
- Incident Responders who understand your network, operations, and needs
- A complete incident response plan enabling your organization to act quickly
The Process
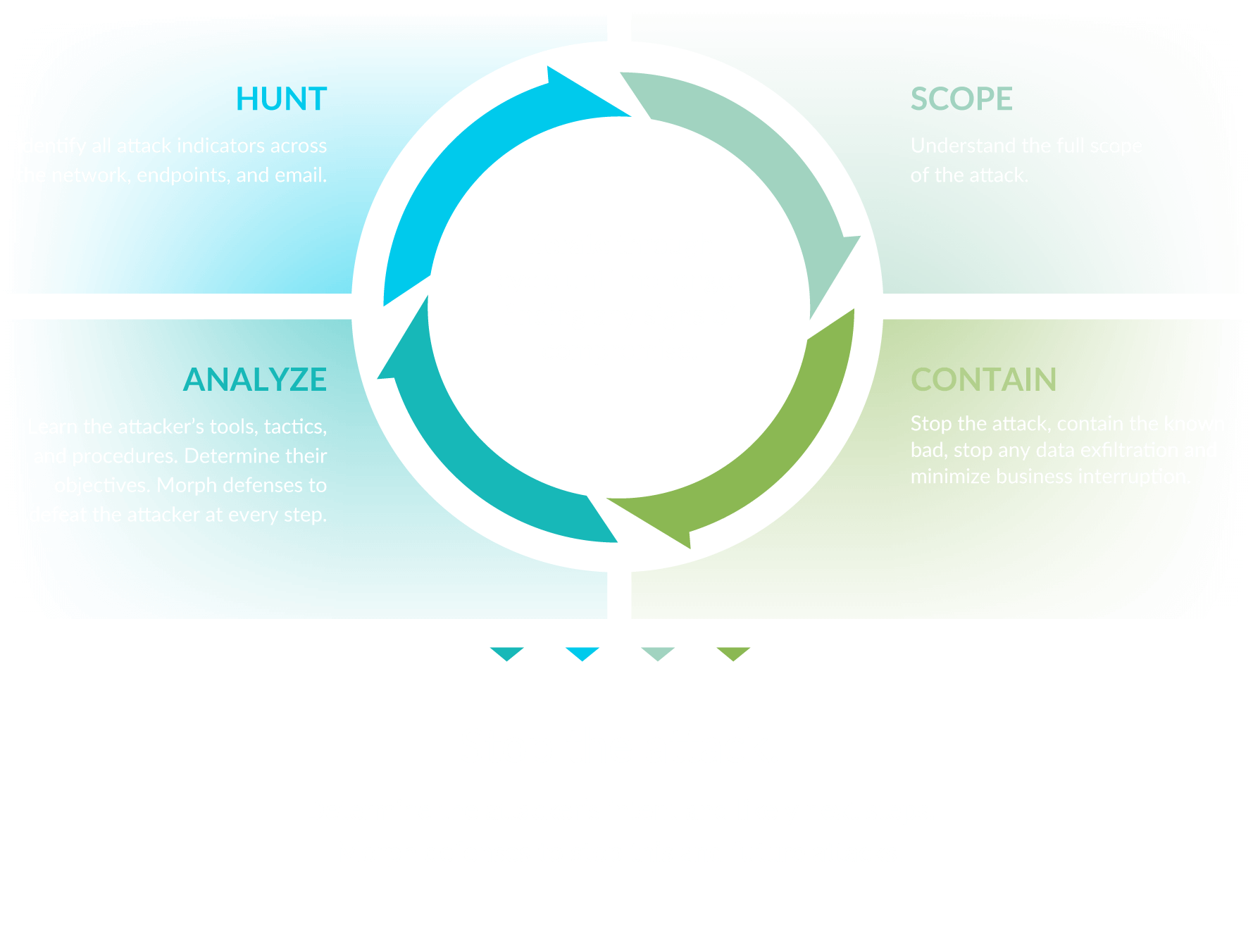
Scope
Identify assets/data potentially affected.
Contain
Stop the attack. Contain the known bad, stop any data exfiltration. Minimize business interruption.
Analyze
Identify the attacker’s activities, tools, and tactics.Identify new or more efficient attack indicators. Determine the attacker’s objective.
Hunt
Hunt for new/more efficient attack indicators across the network.
Remediate Often
Remediate compromised assets. Restore business operations that were impacted. Develop/implement a strategy to prevent future attacks.
What we deliver your organization
-
A 24x7x365 always-on Incident Response team
-
A dedicated team of Reverse Engineers to analyze malicious files
-
An experienced team of intrusion analysts to track and hunt your adversaries
-
A clearly defined contract with agreed upon terms and rates
-
Incident Responders who understand your network, operations, and needs
-
A complete incident response plan enabling your organization to act quickly